Protect Your iPhone from Hackers with These Essential Tips
Your iPhone can be hacked, but don't panic! We've got a few tips and tricks to protect your iPhone data and strengthen your phone's security.


Can someone hack my iPhone? How do I know if my iPhone is hacked? These are questions our readers ask a lot. The answer is Yes. iPhones can be hacked, even with the ever-increasing layers of security Apple implements to protect our devices. With your safety and sanity being a top priority in this technological world, let's take a look at how you can protect your iPhone from hackers and viruses.
Related: 10 iPhone Security Mistakes You're Making & How to Fix Them
Protecting iPhone from Hackers: Basic Dos & Don’ts
While it’s not worth panicking over, it’s good to exercise caution to not unwittingly allow hackers access to our devices. You can do a lot to secure your iPhone and protect it from possible hackers, but let's first cover the basics of how to secure your iPhone from hackers.
1. Don't: Jailbreak
The number one piece of advice for keeping hackers away from your iPhone is this: never jailbreak your device. Jailbreaking allows iPhone owners to access apps and software not available in the Apple ecosystem, but it also exposes your phone to viruses and other malware. Also, once you've jailbroken your iPhone, you've also voided your warranty, so you won't be able to get help from Apple if something goes wrong with your device.
2. Do: Update iOS Frequently
A lot of iPhone users may be skeptical of this advice, but updating your iOS and iPadOS devices to the latest software is the absolute best way to make sure your devices are as protected from hackers as possible. That’s because with each update, Apple improves security features and fixes any previously overlooked weak points that might allow hackers access.
The first couple of weeks after an iOS release often reveal problems with the update itself. This is why I highly recommend you update iOS regularly on your phone, but wait a couple of weeks after the new version is released. Unless the update is meant to address a known, serious security concern, in which case, you should install the new version on your device as soon as possible. To update your device:
- Open the Settings app.
- Select General.
- Tap Software Update.
- If an iOS or iPadOS update is available, follow the prompts to download and install.
3. Don't: Engage with Suspicious Messages
You must be cautious online, in messages & when opening emails. A common way hackers can get to your iPhone is through malware links and scammy emails. You click a link in an email and unbeknownst to you, the link installs software that gives the hacker access to your iPhone. A good rule of thumb is to only open things (links, messages, emails) from sources you trust. This means:
- If you’re browsing on the web, only open a link if you know where it’s going and know that the site it’s on is legitimate.
- If you receive text messages from unknown numbers, look at the message preview to see if it’s someone you know. If the message is strange, asks for something, or contains a link or other suspicious text, simply delete it.
- If an email contains a newsletter you haven’t signed up for, or if it has a link or attachment that you did not request, then delete it. Sometimes your friend's email or message accounts can get hacked. Then the hacker sends emails or messages to everyone they have addresses for. So I'm going to repeat this: never open an attachment or link from an email or text unless you specifically requested it, even if it is from someone you know.
- When entering information into a website, pay attention to make sure the website is legitimate.
Also, be wary of hackers and scammers posing as companies like PayPal and Apple. I’ve gotten fake PayPal emails in the past telling me I’d been locked out of my account and that I need to click somewhere and sign in. It looked completely legit. I clicked on the link, started to enter my info, and happened to look at the URL and see that it was a subtle variation of PayPal and not PayPal itself. Luckily, I caught it in time. Even though I’ve been on the internet since it started, those hackers almost got me. Stay vigilant, my friends.
4. Do: Change Your Apple ID Password Regularly
As noted above, but worth saying again and again: your Apple ID is incredibly important to your iPhone’s overall security. It's the one password to rule them all. If your Apple ID is compromised, the hacker will have access to your iCloud, your iCloud keychain, your everything. Regularly changing your Apple ID password adds an additional level of security: it ensures that even if a hacker gets ahold of your password, it won't be valid for long. I recommend creating a new Apple ID password every six months. If you have two-factor authentication enabled, you can change your Apple ID password right on your device. To do so:
- Open the Settings app.

- Tap your Apple ID at the top.
- Select Password & Security.
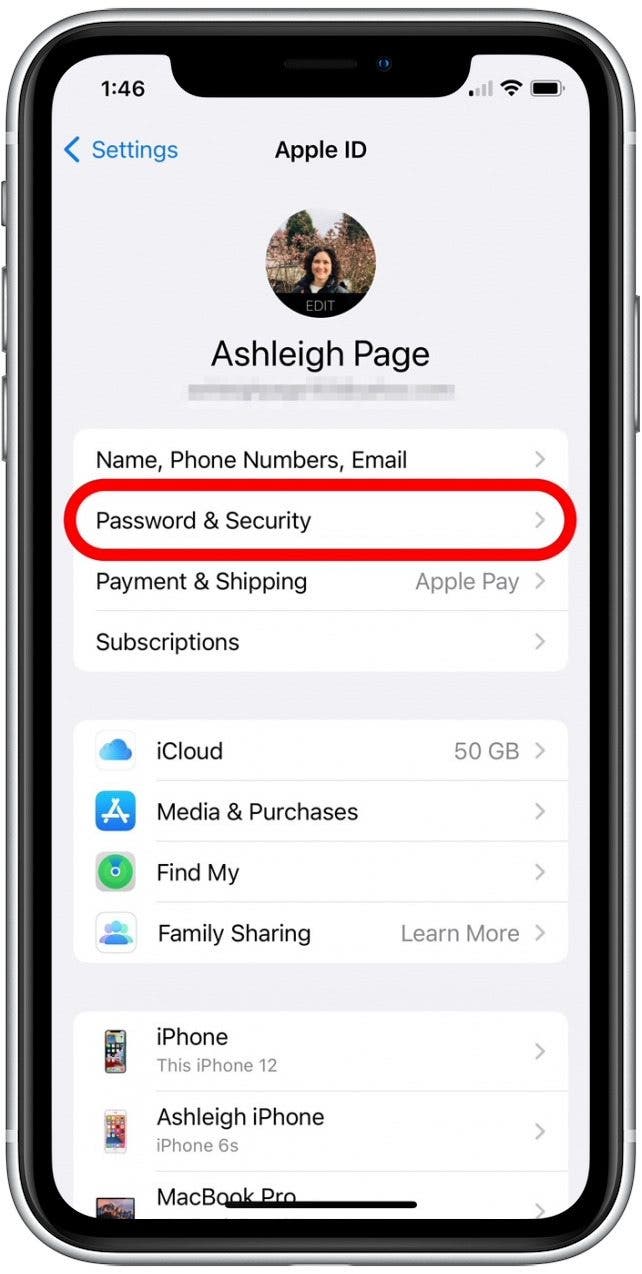
- Tap Change Password.
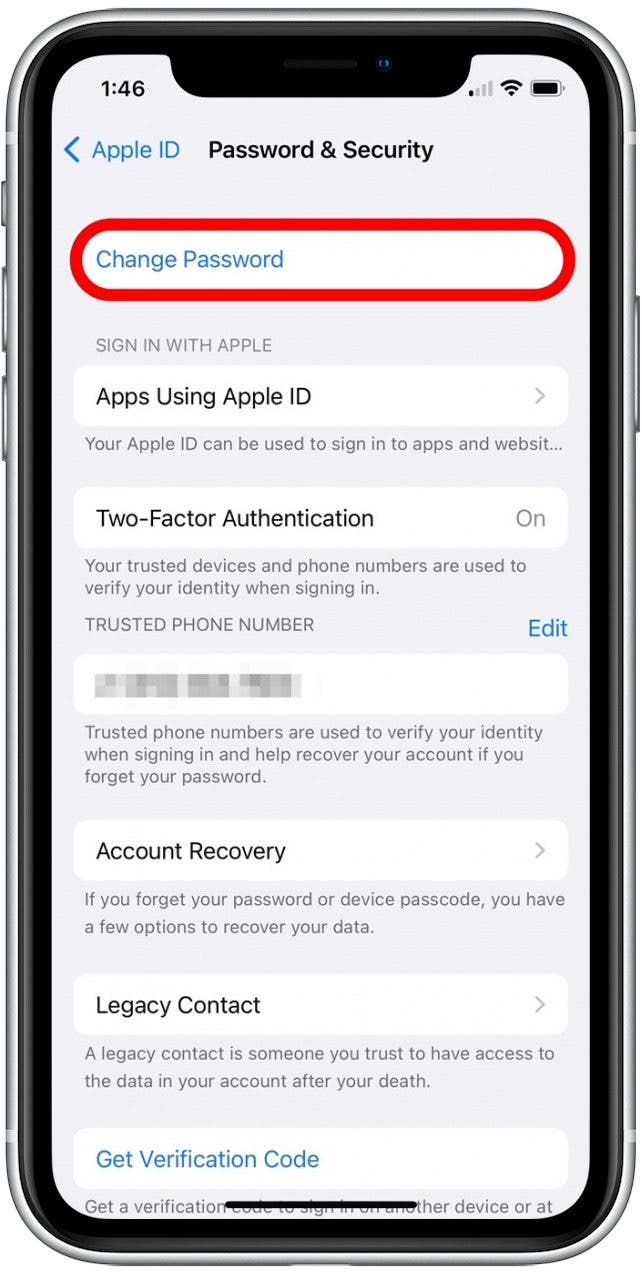
- You'll be asked to enter your current iPhone Passcode.
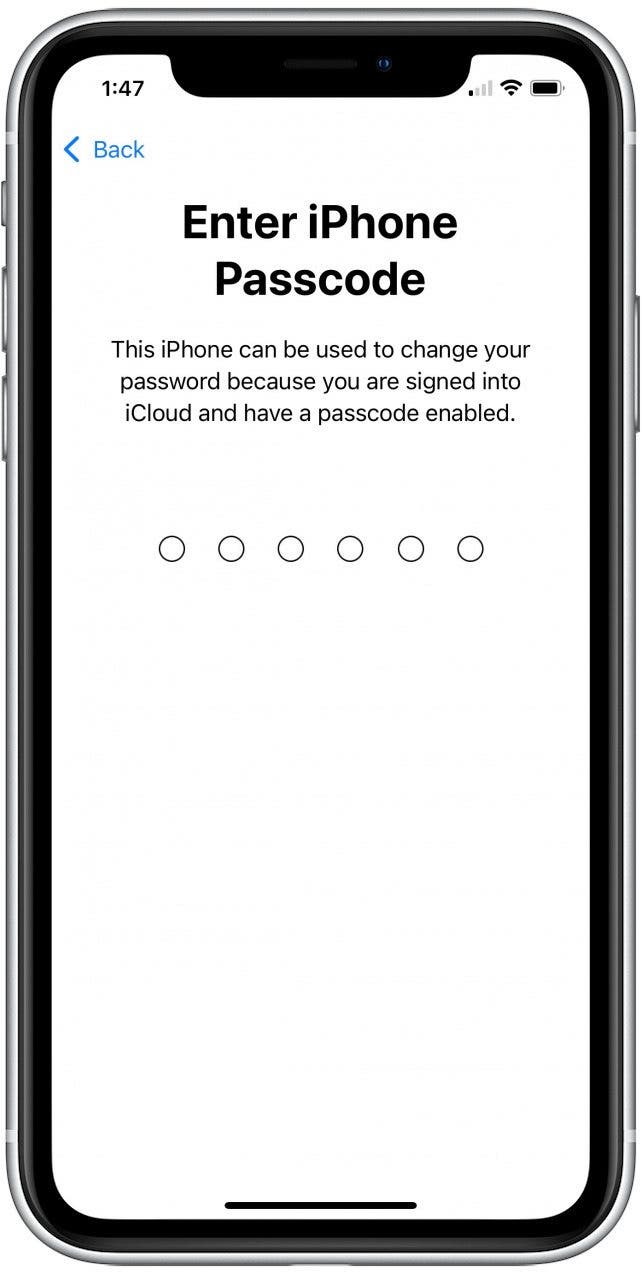
Once you've verified your identity by entering the passcode, follow the prompts to finish resetting your iPhone passcode.
5. Don't: Use Non-Secure Wi-Fi or Logins in Public
Public Wi-Fi is one of the easiest ways to get hacked since public networks are inherently less secure. For paying bills, logging into accounts, and other private activities, it’s highly recommended you use a closed Wi-Fi network, like the one you may have set up at home. A lot of people need to use public Wi-Fi as they do the majority of their work in cafes or have spotty cellular service away from home. If that’s you, consider using a Virtual Private Network (VPN), which will create a private security net around your internet activity.
6. Do: Use Only Trusted Charging Stations
In the last few years, you may have noticed charging stations popping up in airports, cafes, and other public places. While these stations are designed to be convenient for our modern lives, they aren't guaranteed to be secure. Lightning cables work for transmitting data as well as charging, so clever hackers will create false "charging ports" in public places that, in addition to supplying power, try to access your iPhone's data. What's more, once your iPhone has been paired via charging cable to a juice-jacking charging station, your device can be wirelessly accessed at any time without your knowledge, as long as the hacker is within range of your wireless network.
The easiest way around this is to keep a small battery pack with you to charge your devices when they’re low. That way, everything is charged at home, and you have extra power on-the-go. You can also buy a data-blocking charging cable to use while out and about, though I haven't been able to find an Apple-certified one. If you find one, please link to it in the comments! As a third option, turn on your iPhone's Lock screen and then don't use the phone while it's charging at the public station; this way, your data is secured while your device charges.
8 Additional Tips & Tricks to Beef Up your iPhone Security and Avoid Hackers
While the section above focused on the basics of iPhone security, the tips below will help you implement additional safeguards. If you're interested in learning more about iPhone security, consider signing up for our free Tip of the Day Newsletter. Now, here are some further steps detailing how to protect your iPhone from hackers and cybercrime.
1. Keep Your Accounts Secure: Use iCloud Keychain to Generate Unique Passwords
The most serious vulnerability on your iPhone isn't your iPhone itself, but the passwords used on your iPhone to access your data. If you use the same password on multiple websites or services, then you're at risk. Hackers target websites and services that don't seem like they would hold valuable information, like a forum that requires a login. When the hackers get in there, they harvest large lists of passwords. The hackers know that some of those same credentials will have been used in other, more important services, like iCloud. Next, they try all the usernames and passwords they got from the low-security service on iCloud and now and then, they get lucky.
Hackers usually aren't after you personally, so anonymity isn't a good defense. They may not even know your name. If they manage to penetrate a website that has a password of yours, and you used that same password with your Apple ID, they may get onto your iCloud account. They might place files on your iPhone with iCloud, see your photo stream, send emails using your accounts, or mine your personal data from your iCloud backups.
Fortunately, Apple has an easy-to-use solution in iCloud Keychain. This service generates secure passwords and stores them, so you don't have to remember them, and so every password is unique. If you're interested in more information about Apple’s iCloud Keychain, you can also check out the resources below:
- How to Enable iCloud Keychain
- How to Create and Remember Unique Passwords with iCloud Keychain
- How to Eliminate Duplicate Passwords with Apple's Password Manager
If you use iCloud Keychain, you don’t have to worry about remembering your passwords, or about duplicate passwords. But there is a downside: anyone who gets into your iCloud account will have access to all your passwords. You have to make your Apple ID really, truly secure. Use two-factor authentication, which is described in further detail below.
2. Keep Your Apple ID Safe from Hackers: Enable 2-Factor Authentication
You can enable two-factor authentication to use a trusted device to log in to a new device. For example, say you got a new iPad. When you go to sign in with your Apple ID for the first time, your other trusted devices like your iPhone will receive a notification asking for approval. If allowed, your iPhone will display a verification code. Once you enter the verification code on your iPad, the device is approved. This feature works so well because anytime someone tries to log in to your Apple ID account, you’ll get a notification and have the ability to approve or deny the attempt. To use this feature, you need to have iOS 9 software or later.
3. Keep Your iPhone Safe from Hackers: Switch to a 6-Digit or Longer Device Passcode
Apple has made six-digit passcodes the default for a while now, but many users prefer to continue using a four-digit code or no code at all. While it may seem like an inconvenience to add two extra digits to your passcode, it’s worth the added security. Your device passcode should be unique and hard to guess. Nothing like 1111 or 123456! There are one thousand possible combinations of four numbers and one million possible combinations of six. Pick something random. You'll be entering it fairly often, so it should be easy to remember. If you're really serious about keeping your ID safe from hackers, you could consider setting an even longer passcode with both numbers and letters. I strongly recommend changing your device passcode to a custom numeric code or an even more secure custom alphanumeric code.
4. Keep Your iPhone Secure: How to Disable Siri on Your Lock Screen
I hesitated to include disabling Siri on your Lock screen. Partially because it’s a feature I use often and therefore wouldn't turn off myself, partially because it’s more of a long shot that someone would hack your iPhone with Siri. However, over the years, there have been instances of someone being able to access private information by using Siri and finding a loophole in the iPhone’s security. Of course, every time one of these loopholes is discovered, Apple fixes it in the next update. But if you’re concerned with someone bypassing your iPhone’s Lock screen, it’s a good final measure to implement.
If you’re more concerned about remote hacking, this tip won’t matter as much to you. But if you’re worried about someone picking up your phone and finding their way in, turning off Siri on your Lock screen is the way to make sure they’ll need your passcode to get in. Here's how to disable Siri on your lock screen:
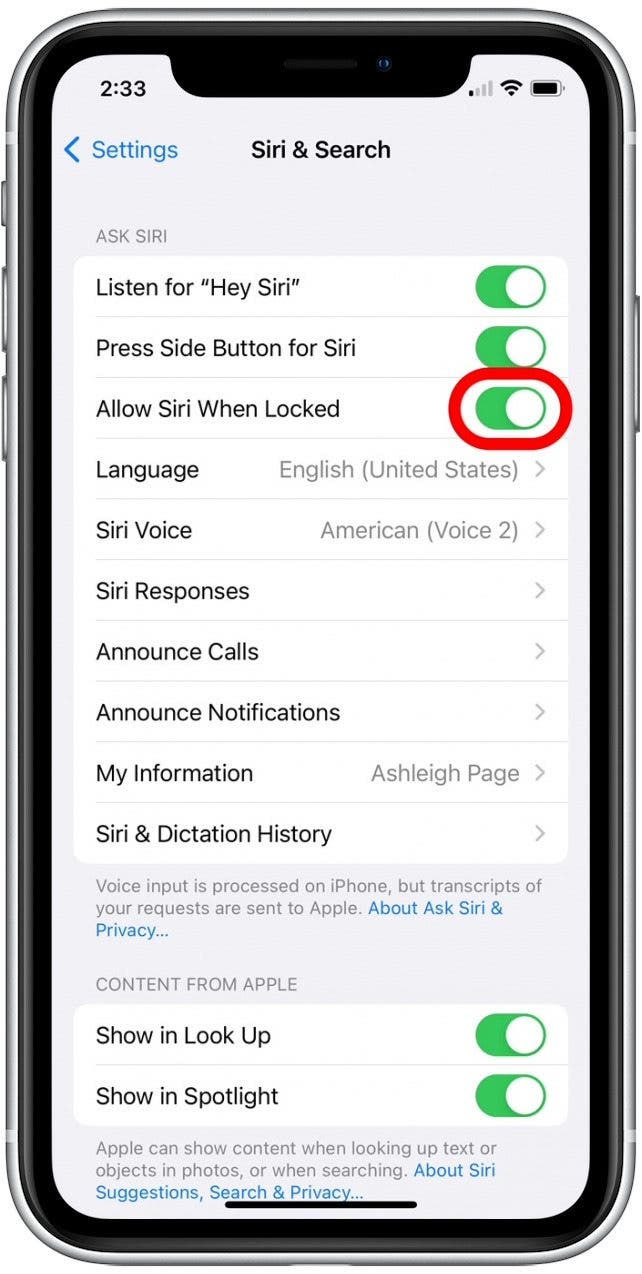
- Open the Settings app.
- Select Siri & Search.
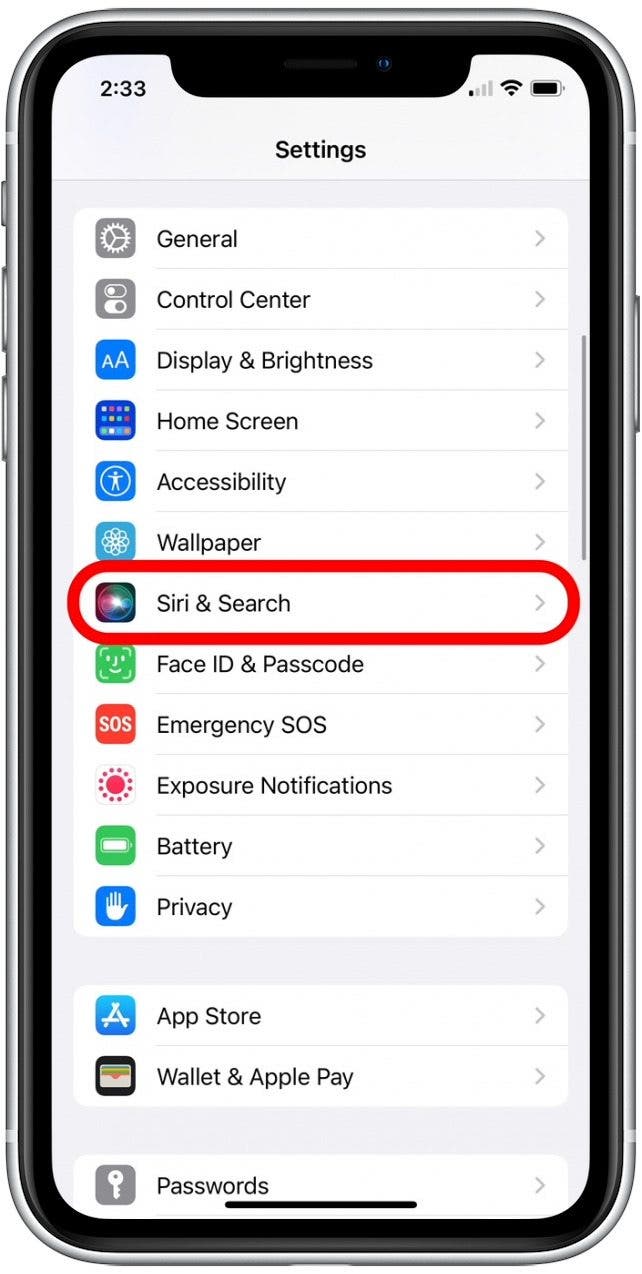
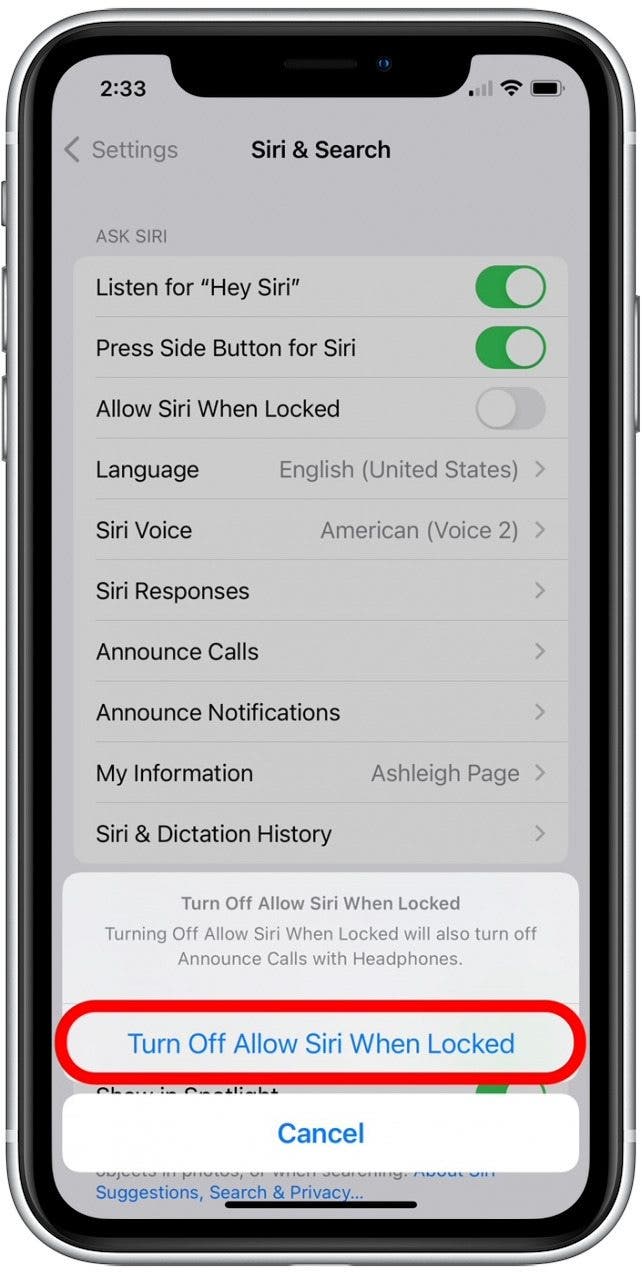
- Tap to disable the Allow Siri When Locked toggle.
- To confirm, tap Turn Off Allow Siri When Locked.
5. Keep the Data on Your iPhone Safe: Erase Data If Lost
This is a no-brainer. When you turn on Find My for your iPhone or iPad, you can see the location of your phone or tablet from any of your other devices or via iCloud.com. While it’s not recommended you personally track down an Apple device that’s fallen into the hands of a thief, the Find My app will allow you to find your iPhone or iPad if you lose it. However, that’s not why it’s recommended for protecting your device from hackers. The great thing about Find My is that if your device is stolen, you can remotely erase your device so that none of your personal information can be stolen too. If you haven't already, first turn on Find My, then follow the steps below to learn how to erase an iPhone that has been stolen or lost:
- Open the Find My app.
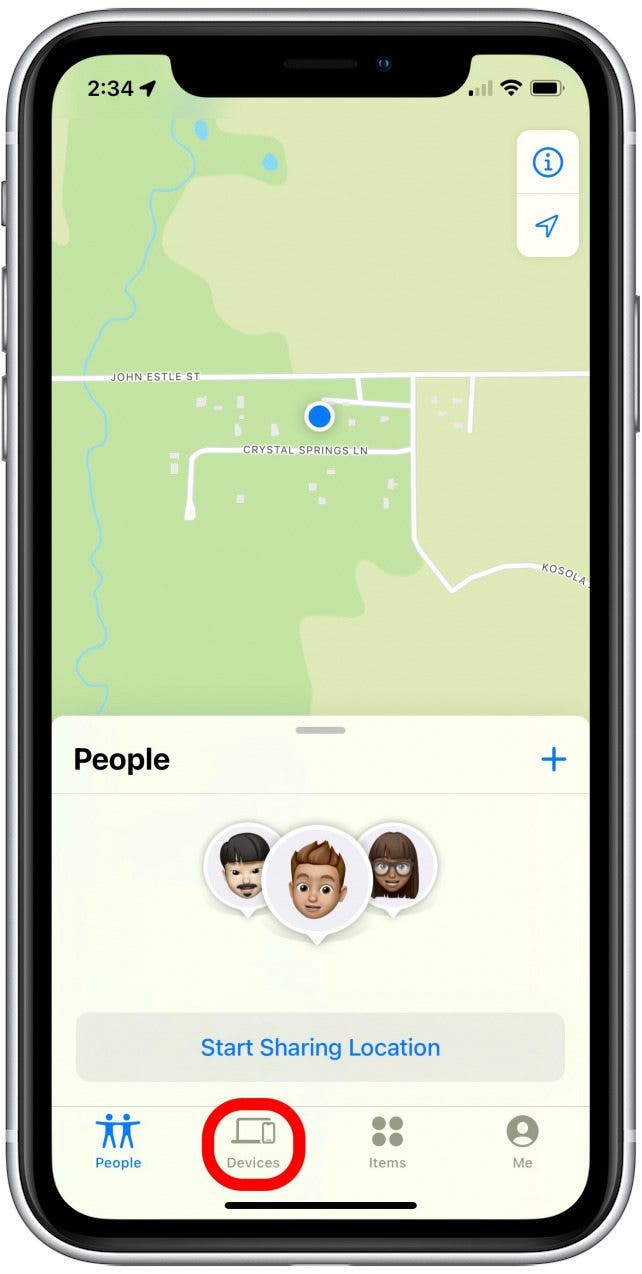
- Tap the Devices tab at the bottom of the screen.
- Tap the name of your iPhone in the list of devices.
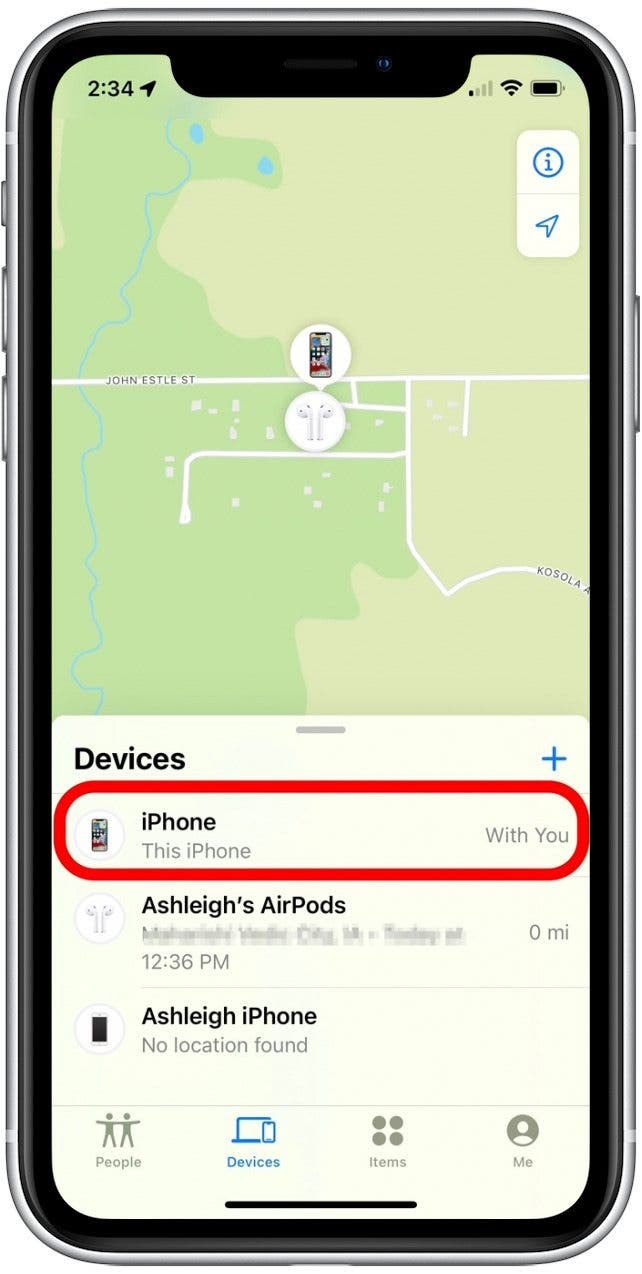
- Scroll down to the bottom and tap Erase This Device.
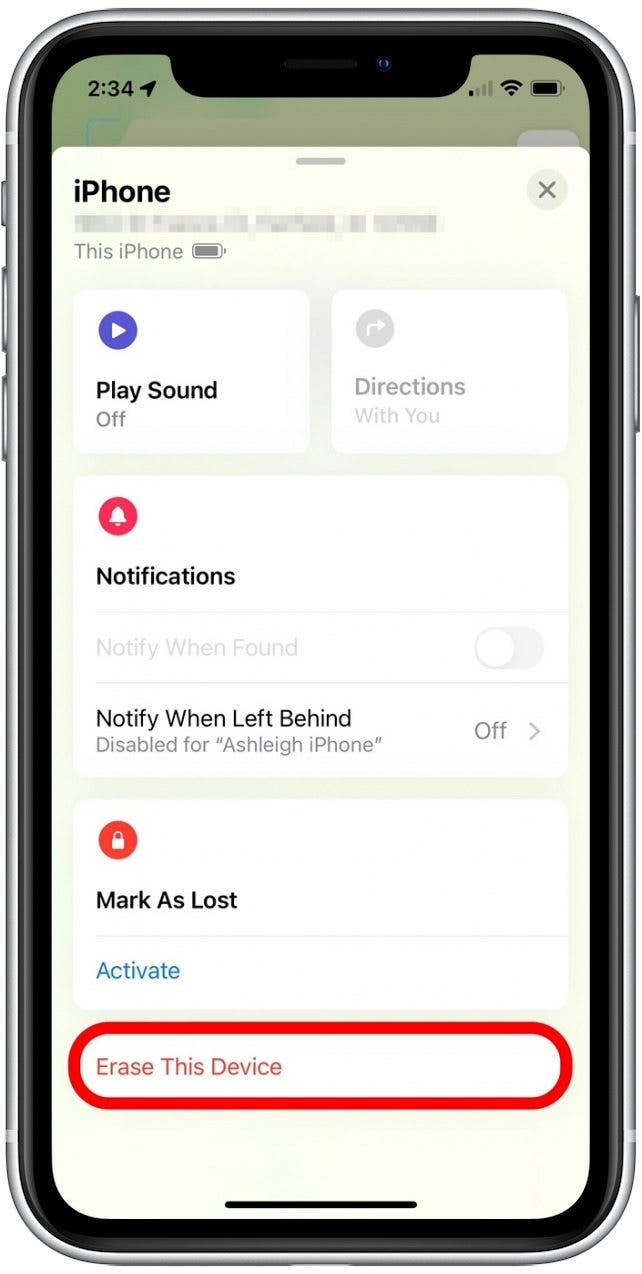
Follow any on-screen prompts to confirm the setup of this feature.
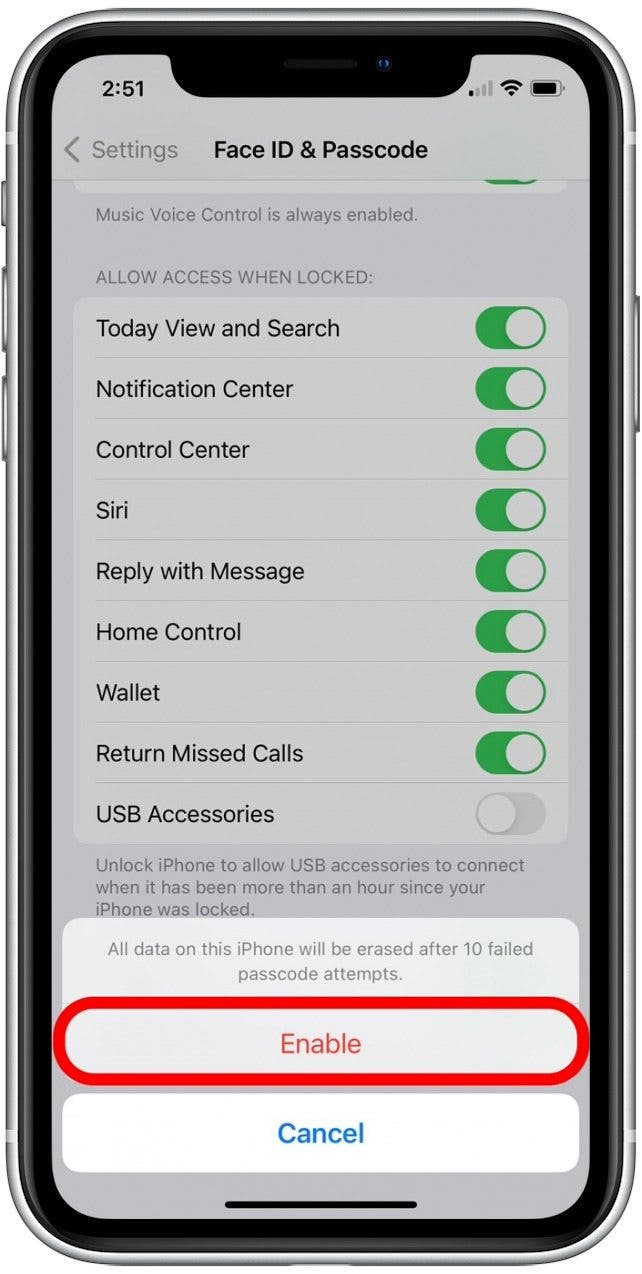
6. iPhone Security: Set Your Phone to Self-Destruct
Okay, so your phone can't really self-destruct, but close enough. You can turn on a setting that will wipe your device clean after ten consecutive failed passcode attempts. I would only turn this setting on if you’re super concerned about some of the information you have on your phone, and you have automatic iCloud backups enabled. People with children should be especially careful, since ten failed attempts will erase everything, and you'll need to restore your phone from a backup. But, it is a fantastic security measure. Let's cover how to turn on Erase Data:
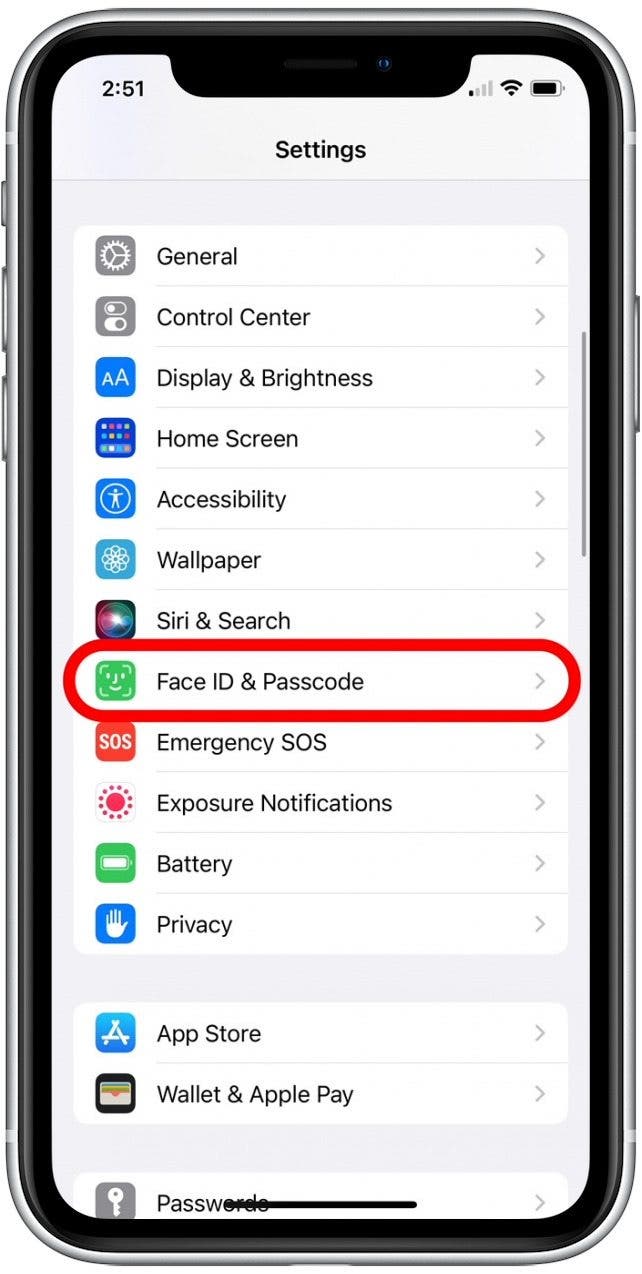
- Open the Settings app.
- Select Face ID & Passcode (or Touch ID & Passcode for iPhones with a Home button).
- Enter your passcode.
- Scroll down and tap the Erase Data toggle.
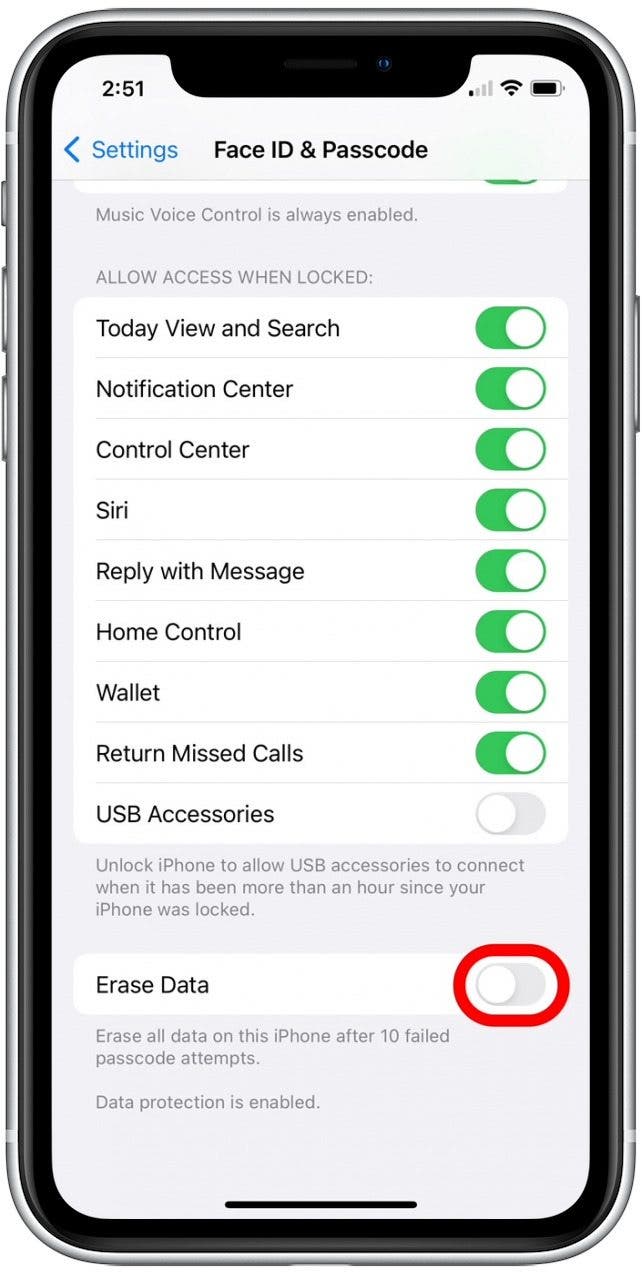
- Tap Enable to confirm.
7. Hacker Protection: Use an End-to-End Encryption Service
Did you know that it's possible for hackers to spy on your messages and calls, track your location, and even intercept two-factor authentication codes if they know your telephone number? Signaling System Number 7 is part of the global network that connects our cellphones. This set of protocols enables cell phone service providers to send and receive information about calls and texts so they can properly bill their customers, but it comes with a price. Government entities and hackers can exploit SS7 to spy on literally anyone's cell phone as long as they know their phone number, and the target won't know it's happening at all.
Although it's highly unlikely that anyone would use SS7 to hack your iPhone, it's good to know it's a possibility so you can protect your privacy. Download and use an end-to-end encryption app such as Signal to send and receive calls and messages to keep all your communications private, especially if you need to share something important. As an additional security safeguard, you can use a secure Wi-Fi network rather than your carrier to send and receive calls and messages.
8. Hacking Apps for iPhone: Keep Your Device Free from Tracking Apps
There’s a set of app developers constantly working to develop hacking apps to sell to the public. They’re usually disguised as an app with a different feature set; you download it for free, and it starts doing things behind the scenes that you wouldn’t want. iPhones don’t need to be jailbroken for these to work; although it’s much easier to install a spying app on a jailbroken phone, it’s possible to use one on a device with factory settings as well. Apple’s App Store is always on the lookout for these illicit apps, but they can sneak through the cracks. Try to use apps from reputable companies with lots of reviews, and only apps that have been updated recently.
I hope these tips covering how to secure your iPhone from hackers have been helpful! Even if you only implement a couple of these, you are already on your way to stronger data and iPhone security.

Conner Carey
Conner Carey's writing can be found at conpoet.com. She is currently writing a book, creating lots of content, and writing poetry via @conpoet on Instagram. She lives in an RV full-time with her mom, Jan and dog, Jodi as they slow-travel around the country.
 Leanne Hays
Leanne Hays
 Olena Kagui
Olena Kagui
 Rhett Intriago
Rhett Intriago
 Amy Spitzfaden Both
Amy Spitzfaden Both
 Cullen Thomas
Cullen Thomas

 August Garry
August Garry


 Rachel Needell
Rachel Needell