iPhone Life - Best Apps, Top Tips, Great Gear
Apple TV VPN: Everything You Need to Know
By Olena Kagui
When it comes to getting a VPN for Apple TV, there are many factors to consider, such as cost, compatibility with your favorite streaming services, and the location and number of VPN servers in your area. We’ll give you a list of popular VPN Apple TV options and teach you how to set them up on your device.
Spring Rumors: AI Coming to iOS 18 & M4 iPad Pro
By Susan Misuraca
In episode 210, David and Donna cover all the rumored AI features coming to the iPhone with iOS 18, from auto-writing texts to summarizing articles in Safari. Other topics include Apple’s May 7 event, where they plan to debut the M4 iPad Pro and new haptic-powered Apple Pencil.
- 1 of 2394
- next ›
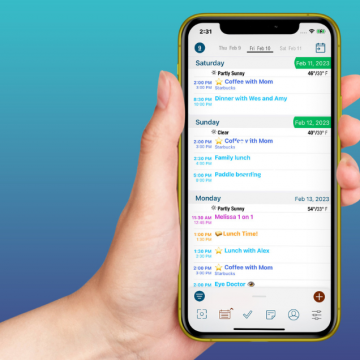
How to Organize Your Calendar in 2024
(Sponsored Post) By Rachel Needell on Thu, 04/25/2024
Apple is pretty good about updating its products, but it seems to have forgotten about the Calendar app and its many downsides. The makers of Informant 5, on the other hand, do not forget to regularly improve their app based on user experience. The latest updates to this calendar and task-management app are a productivity game-changer.
Turn Off Link Thumbnails in the Messages App on iPhone
By Rhett Intriago
Link previews in Messages are thumbnails that show a site's chosen banner in a text message, along with the link. This can be useful for identifying what the link contains before you open it. However, it can also be a bit of an annoyance if you prefer to keep your messages less cluttered. Let’s take a look at how to turn off iMessage link previews.
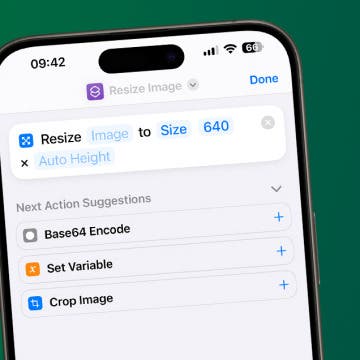
How to Resize an Image on iPhone
By Olena Kagui
Learn how to make a picture smaller or bigger or change its aspect ratio on your iPhone using native and third-party apps. We'll teach you how to use the Shortcuts app to manually resize photos, the Photos app to crop photos, and the Messages app settings to automatically send lower-quality photos.
Home Button on iPad Not Working? Here’s the Fix!
By Leanne Hays
Why has your Home button stopped working on your iPad? You may need to update your software, reset your settings, or give the Home button a good cleaning. We'll show you how to get your iPad's Home button responding again.
Apple's 'Let Loose' Event on May 7: New iPads & Accessories
By Olena Kagui
While Apple enthusiasts have been anticipating the annual WWDC keynote, happening June 10, the May 7 Let Loose event announcement has come as a happy surprise. Apple hasn’t provided a lot of information about this event, but because of the event photo featuring an Apple Pencil and the fact that iPads are often announced in the spring, we are expecting new iPads, an Apple Pencil, and maybe other Apple accessories too.
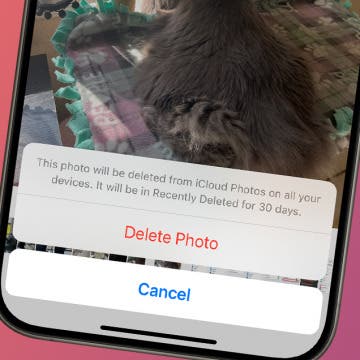
Fixed: iPhone Won’t Let Me Delete Photos
By Rhett Intriago
Photos tend to take up the most storage on any phone, so when storage is running low, the first thing you will likely want to do is delete photos. However, you might occasionally run into a bug where your iPhone won’t let you delete photos. Let’s find out how you can fix this issue and finally clear up some storage.
Answered: What Are Haptics on iPhone?
By Rhett Intriago
While fiddling with your iPhone’s settings, you’ve probably come across something called System Haptics. You might not have even noticed a huge difference when turning it off or on. So what are haptics on iPhone and what do they do? Let’s find out!
How to Use Personal Voice on Your iPhone
By Rhett Intriago
Have you ever wanted a computer-generated version of your own voice? The iPhone's Personal Voice feature allows you to do just that. This accessibility option is a great tool for those at risk of losing their voice, but it can be used by anyone. Below, we’ll dive into what Personal Voice on iPhone is and how to make the most of this handy feature.
Check Busy Times for Nearby Businesses
By Rhett Intriago
Want to check how busy your favorite restaurant is before you head out? Google Maps makes it easy to see whether a business is currently busy and when it is busiest and least busy. Here’s how to see how busy a place is on Google Maps.
How to Unlock a Keyboard on Your Mac—the Easy Way!
By Olena Kagui
Unlocking your Mac keyboard is easy, but the steps depend on whether you have a built-in, Bluetooth, or third-party keyboard. It may seem that your Mac keyboard isn't working when it is actually locked. We'll teach you how to unlock the keyboard on your Mac without a hassle!
Answered: What Is the Flower on iPhone Camera?
By Rhett Intriago
If you have a Pro iPhone, you've probably noticed the flower icon in your iPhone camera when taking photos. Usually, this icon only appears when you're taking close-up photos. Below, we'll cover how to use and disable the Macro mode flower icon.
How to Drop a Pin on iPhone in Google Maps
By Leanne Hays
How do you mark a location on Google Maps on an iPhone? You drop a pin! Here's how to drop a pin on Google Maps on your iPhone, so you can save favorite locations, your parking spot, your location at the moment, and more!
Why Is Safari So Slow on iPhone & iPad
By Leanne Hays
Why is Safari so slow on my iPhone? If Safari is slow to load, you may have too many tabs open or not enough iPad or iPhone storage available. There are a few other ways to fix Safari acting slow, too. Read on to find out!
iPhone or iPad Stuck in Headphone Mode? Here’s the Fix!
By Leanne Hays
If your iPhone or iPad is stuck in headphone mode, you won't be able to hear any audio from your device except via headphones. There are several reasons why your device might be stuck in headphone mode: you might have outdated software, a dirty headphone port, water damage, or incompatible headphones. Usually, the issue can be quickly solved by toggling Airplane mode and off. However, if that doesn't work, we'll cover the common solutions to get your audio working again!
How to Fix Apple Watch ECG Not Working
By Rhett Intriago
The Apple Watch ECG is one of the most useful apps you can have on your device. You can use it to keep track of your heart health and share the results with your doctor. However, if the ECG is not working, you won’t be able to see the results you need. Here’s what you can do to fix it.
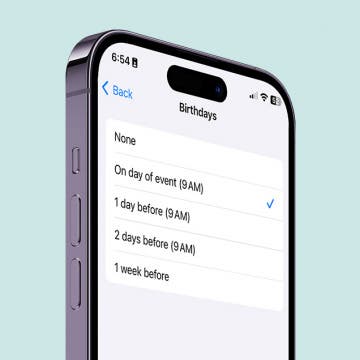
How to Get Automatic Birthday Reminders on iPhone
By Rachel Needell
Nobody likes to miss their friend's birthday. Especially if you don't use social media, it can be easy to forget the exact day a person was born. That's why I like to have my iPhone send me notifications automatically on an important person's birthday. Here's how to set it up!
Decipher Laundry Symbols with Your iPhone Camera
By Rhett Intriago
Everyone has seen the mysterious laundry symbols on their clothes, but nobody seems to really know what they mean. I, for one, always have to look up what the symbols actually mean to make sure I’m washing my clothes correctly. Luckily, the latest iOS software makes it easy to identify laundry tag symbols.